Update 10-2021: I have updated this post at the end since it is for (some) new customers possible to configure only VLAN300 for both internet and television. So a router with built-in switch is not required.
The amount of configuration information on T-Mobile Thuis fiber connections with EdgeRouter equiptment is a bit scarce. The configuration looks a lot like the
KPN Fiber and Vodafone configuration, but is slightly different.
I have chosen to use a fiber to ethernet converter, the TP-Link MC220L. But I think that I will buy the new EdgeRouter 4 when it comes to the Netherlands. Which is roughly the EdgeRouter X with fiber port and the EdgeRouter Lite combined. But for now, this configuration is based on the EdgeRouter Lite 3.
T-Mobile and their VLAN’s
At first, we need to know that T-Mobile seperates the internet and IPTV connection using VLAN’s. VLAN300 is used for the internet traffic and VLAN640 is used for the IPTV traffic. T-Mobile seperates this traffic in their own router. We will have to do the same in our configuration. Later on, we will devide our connection using a bridge in to two seperate VLAN’s. These VLAN’s will be made available in the switches.
My set-up
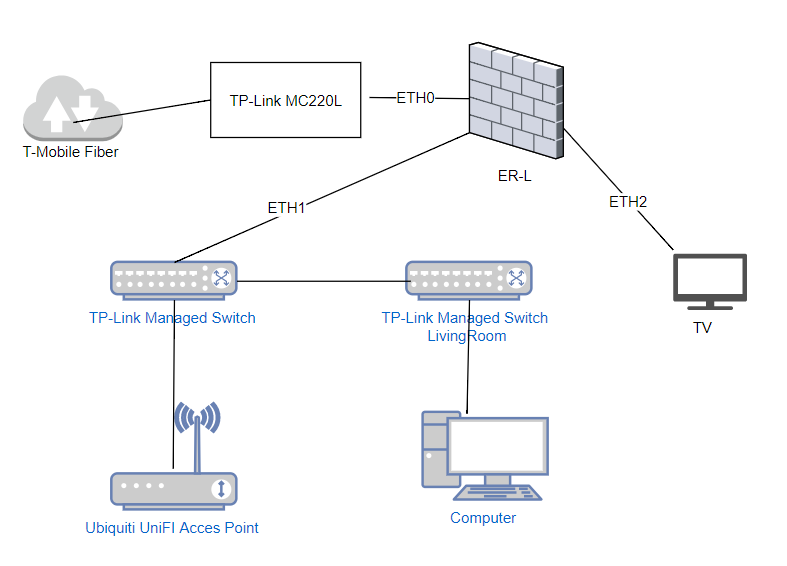
My set-up is fairly basic. In the diagram below, I have drawn out my setup. Let me talk you through it; The fiber connection comes in at the fiber converter and is attached to the ETH0 interface of the EdgeRouter-Lite (ER-L). The LAN connection is on ETH1 and is connected to an
managed ethernet switch. The ETH2 is (in my case) directly attached to the IPTV box.
The switch has (multiple) Ubiquiti UniFi access points attached, a few wired devices (laptop, Ikea Tradfri gateway, a computer) and a (trunk) connection to another managed switch in the living room for my Playstation, TV and HTPC.
The configuration of the EdgeRouter Lite
Below here is a copy of my configuration, with a few details cleared. These are port mappings, static IP assignments and passwords. What this configuration does is the following:
- Create ETH0 for the WAN connection, with DHCP enabled so it receives it’s (external) IP from T-Mobile
- Split ETH0 in to ETH0.300 for the VLAN300 and ETH0.640 for the VLAN640 traffic (internet and iptv)
- Creathe ETH1 with local IP adresses in the 192.168.0.0/24 range. ETH1 has VLAN300 attached for the internet traffic.
- Creathe ETH2 without an IP adres (T-Mobile will handle that itself) with VLAN640 attached for IPTV.
- Create a few default firewall rules to block harmful traffic.
- Allow NAT for VLAN300 for the internet traffic
- Enable an IGMP proxy for IPTV
These configurations can be done using the Config Tree in the console, from top to bottom.
Robin@vanbruggen:~$ show configuration | no-more
firewall {
all-ping enable
broadcast-ping disable
ipv6-receive-redirects disable
ipv6-src-route disable
ip-src-route disable
log-martians enable
name WAN_IN {
default-action drop
description "WAN to internal"
enable-default-log
rule 40 {
action accept
description "Allow established/related"
log enable
protocol all
state {
established enable
invalid disable
new disable
related enable
}
}
rule 50 {
action drop
description "Drop invalid state"
log enable
protocol all
state {
established disable
invalid enable
new disable
related disable
}
}
}
name WAN_LOCAL {
default-action drop
description "WAN to router"
enable-default-log
rule 30 {
action accept
description "Allow established/related"
log disable
protocol all
state {
established enable
invalid disable
new disable
related enable
}
}
rule 40 {
action drop
description "Drop invalid state"
log disable
protocol all
state {
established disable
invalid enable
new disable
related disable
}
}
}
receive-redirects disable
send-redirects enable
source-validation disable
syn-cookies enable
}
interfaces {
bridge br0 {
aging 300
bridged-conntrack disable
hello-time 2
max-age 20
multicast enable
priority 32768
promiscuous disable
stp false
}
ethernet eth0 {
address dhcp
bridge-group {
}
duplex auto
speed auto
vif 100 {
description MGT
mtu 1500
}
vif 300 {
address dhcp
description Internet
firewall {
in {
name WAN_IN
}
local {
name WAN_LOCAL
}
}
}
vif 640 {
bridge-group {
bridge br0
}
description IPTV
}
}
ethernet eth1 {
address 192.168.1.1/24
description Local
duplex auto
speed auto
}
ethernet eth2 {
bridge-group {
bridge br0
}
description IPTV
duplex auto
speed auto
vif 640 {
bridge-group {
bridge br0
}
description IPTV
}
}
loopback lo {
}
}
protocols {
igmp-proxy {
interface eth0 {
role disabled
threshold 1
}
interface eth0.300 {
role disabled
threshold 1
}
interface eth0.640 {
alt-subnet 0.0.0.0/0
role upstream
threshold 1
}
interface eth1 {
role disabled
threshold 1
}
interface eth2 {
alt-subnet 0.0.0.0/0
role downstream
threshold 1
}
}
}
service {
dhcp-server {
disabled false
hostfile-update disable
shared-network-name LAN1 {
authoritative enable
subnet 192.168.1.0/24 {
default-router 192.168.1.1
dns-server 8.8.8.8
dns-server 8.8.4.4
domain-name vanbruggen
lease 86400
start 192.168.1.100 {
stop 192.168.1.250
}
}
}
use-dnsmasq disable
}
dns {
forwarding {
cache-size 150
listen-on eth1
listen-on eth2
}
}
gui {
http-port 80
https-port 443
older-ciphers enable
}
inbound-interface eth0.300
inside-address {
address 192.168.1.200
port 32400
}
log disable
protocol tcp
type destination
}
rule 5010 {
description "masquerade for WAN"
log disable
outbound-interface eth0.300
protocol all
type masquerade
}
}
ssh {
port 22
protocol-version v2
}
unms {
disable
}
}
system {
host-name vanbruggen
login {
user Robin {
authentication {
encrypted-password ****************
}
level admin
}
}
ntp {
server 0.ubnt.pool.ntp.org {
}
server 1.ubnt.pool.ntp.org {
}
server 2.ubnt.pool.ntp.org {
}
server 3.ubnt.pool.ntp.org {
}
}
offload {
hwnat disable
ipv4 {
forwarding enable
pppoe enable
vlan enable
}
}
syslog {
file dhcpd {
archive {
files 5
size 5000
}
facility local2 {
level debug
}
}
global {
facility all {
level notice
}
facility protocols {
level debug
}
}
}
time-zone Europe/Amsterdam
}
A screenshot from the EdgeRouter Dashboard after the configuration:
Switch configuration
In order to correctly browse the internet using the wireless access point (which has a very basic default configuration, nothing special) and/or use the internet on any other wired device, you will have to assign each port to the correct VLAN. If you have extra switches behind the first switch, you will need to configure a
trunked VLAN port and transmit both VLAN’s (300 and 640) on that port.
I have done the following in my switch, a TP-Link TL-SG1016DE. Which is a managed switch. Create VLAN300 and attach it to the correct ports where your (internet) devices are on. Do this in the ‘802.1Q VLAN’ configuration and the ‘802.1Q PVID setting’.
Update: Television without seperate VLAN
It has been a while since I did something with the T-Mobile fiber network. My household has stopped using the T-Mobile television and switched to streaming services only so we have cancelled that subscription and only use the 1000mbit internet connection. I am using the EdgeRouter 6P now.
Last week I was asked to setup a T-Mobile fiber network at someone’s house. I have set it up with the EdgeRouter X SFP. It is also possible with the Edgerouter 6P or another router without the switching chip. I learned that (some?) new customers will get their fiber to the home using a GPON splitter. You will not attach the fiber cable to the router and will have an ethernet cable coming out of the splitter to your router.
I only had to configure VLAN300 and the TV signal was available without having to configure VLAN640. This made the setup very easy. Just a basic router setup, WAN on one of the ethernet ports using VLAN300. You can do this using the basic Edgerouter setup wizard.


Thanks for your blog post.
I’m actually not sure whether igmp proxy is required for T-Mobile. It definitely is for the routed IPTV solution from KPN, but I think that T-Mobile has a simpler approach which just works with the VLANs. Have you managed to get TV to work with your config above?
Hi T. Tanos, I have posted a new article with my new setup. I did not get a fully working scenario woth the EdgeRouter Lite and IPTV. I have replaced the router with the X SFP. I have a perfectly working scenario with both IPTV and internet since then.
Can you tell which SFP module you used (and hence works)?
Hi Jaap, I’ve used the SFP module that comes with the default T-Mobile router. This one works fine with the TP-Link converter or a router with SFP port.
So your internal internet vlan (192.168.x.x/24) is 300 with no IGMP snooping and your tv is in 640 with IGMP snooping?
Hi Dre, Yes I have enabled IGMP Snooping only for VLAN 640. But I need to tell you that I did not get IPTV to run perfectly smooth here.
Hi Robin,
Im currently using KPN and want to go to Tmobile. So now I have the routed IPTV, but with bridged I don’t want to pull an extra wire just for the tv upstairs.
Cant I simply use a managed switch (TL-SG108e) to combine internet and iptv vlans onto one port and send that upstairs to a router so I have the similar bridged setup I now have with KPN?
Or do I need another managed switch upstairs to split the combined vlans to separate ports?
Hi Michiel,
I think that would work, depending on the configurability of the router. You will still need to configure the right VLAN(s) on the port where you connect your IPTV and configure a trunk port on the switch where the router is connected to so that you have both internet and iptv vlan’s available.
I would recommend you to set up a managed switch upstairs and configure a trunk between them. You can add more devices to it, maybe an access point or multiple tv’s as it probably has more ports available than a router. You have to configure the port for your IPTV upstairs with the right VLAN.
With a router you will have somewhat the same setup and will use the internal switch of the router and do the same. You can maybe use the router as an extra access point for your wireless internet clients upstairs.
Thanks Robin for this write up.
I got it working on the edgerouter lite with your guide. Including IPTV through a Zyxel GS1900HP-24 as a switch. Getting the VLAN settings right on the Zyxel was trial and error, but that was also due to my own lack of knoop.
On tweakers.net I did find some additional config which was necessary for the IPTV to work.
configure
set interfaces bridge br0 multicast enable
echo -n 0 | sudo tee /sys/devices/virtual/net/br0/bridge/multicast_snooping
echo -n 1 | sudo tee /sys/devices/virtual/net/br0/bridge/multicast_querier
commit
save
Thank you! I will update the post with that. Thank you for your reply and good to hear that everything is working! Sounds great 🙂
Hi Robin,
thank you for the info, I have t-mobile fiber Internet , I was using Synology router RT1900AC in combination with the media converter, I setup Vlan 300 for internet and everything worked fine,
recently I have replace the Synology router with Edgerouter 10X and followed your config but still did not get it right, I even used the wizard for configuration WAN2LAN2 where you can select internet though vlan but still no internet!!
could It be that there is something more I need to with with Edgerouter 10X than only the config above.
thank you
jay
hi Robin,
i have T-Mobile with the zyxell t-50 (routed iptv?)
ik have it working (routed) only i keep loosing the EPG/Guide info. it looks like this info is gooing out and in on vlan300 and not on vlan640. When i disable the interface with vlan300 and switch channels on the tvbox or reboot the tvbox the info is back. but it wil not update and stops working both working. i can watch tv and have internet.
Martijn
Hi Martijn,
How is the tv box connected? Directly to the router or using a switch? Sounds like VLAN640 is not correctly tagged.
Hoi Robin,
Weet je ook of en hoe het mogelijk is om het IP adres van de SPF glas door te zetten op de ETH1?
Voorkeur is gewoon een bridge (met alle poorten open) met een IP aangeboden op mijn router.
How can i do this with the Edgerouter 6P. (i don’t use the software bridge)
Behind the Edgerouter 6P i have the Edgeswitch connected for lan and additional vlans (guest, iot etc.)
I only need internet and no iptv etc.
Can i connect the FTU to ETH5 SFP on the Edgerouter?
And do i need to configure something on my lan interface for vlan 300?
Or is ETH5 with vlan 300 and ETH.300 for nat masquerade enough?
Hi Hendrik, you should configure on the edgerouter (WAN) on the correct ports and connect the ftu to eth5, thats correct. That should work. Maybe even the wizard in the GUI should do the trick for your config.